|
ISPreview investigate the fraud @ VisualDepth |
Official Investigation It swiftly became clear that we were stuck in a paradox with one certain truth, somebody was lying and we wanted to know who and why (usually money). So from July 4th we began our official investigation, from that point on we chose not to mention VD in such a sense again until it had completed. VD agreed and all comments on the ISP were and would be removed from future news postings. Phase 1: There were three phases to our investigation; phase 1 was to talk with the people (subscribers) involved with the ISP(s) and collect evidence. Phase 2 was for talking with companies and finding out what connections the ISP had, the final phase is this report and the conclusion. Being phase 1 our first port of call was to hall in some VD subscribers who would be willing to help in our investigation. We didn't have to do much as several people came forward and some we already knew (names hidden). These people were 'technically aware', so knew their way around a computer system and understood networks (at least most did). We already knew VD subscribers could connect to EzeSurf and even VD had admitted that, the problem is they put it down to a security fault. What we had to prove was that they were unofficially reselling EzeSurf accounts for a higher price - fraud. This could be done in several ways, by checking the connection logs and physically monitoring the connection. First Result It didn't take long to get the first 'Event
Log' from under MS Windows 2000; you can see it below: 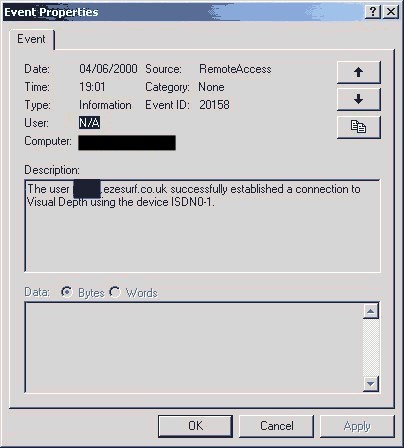 [Print Page | Next Page (4)]>>
Have something
to say? Check out the ISPreview Forum -->
http://www.ispreview.co.uk/cgi-bin/ubbcgi/Ultimate.cgi |