|
ISPreview investigate the fraud @ VisualDepth |
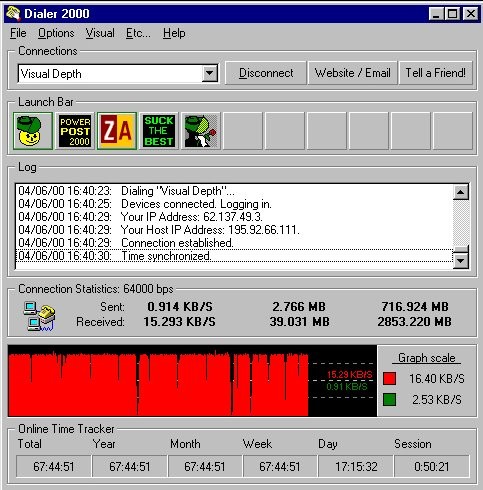
 Sadly this wasn't enough because it didn't show all the details needed to provide an accurate assumption. As such a piece of software known as Dialler2000 was used at the same time to monitor the connection (below):
This gave us the first real proof and evidence that we needed to help track down what was really going on, a single IP (62.137.49.3 - confirm as an EzeSurf IP for that period). One thing VisualDepth slipped up on was that they stated their network was NOT Planet Online (now Energis), so we ran a whois/DNS test on the IP while logged on (below/next): [Print Page | Next Page (5)]>>
Have something
to say? Check out the ISPreview Forum -->
http://www.ispreview.co.uk/cgi-bin/ubbcgi/Ultimate.cgi |