Snooping TalkTalk Security Feature Causes Customer Concern UPDATE2
A number of TalkTalk’s broadband ISP customers in the UK have raised concerns after the provider sent them an alarmist warning email, which without providing any useful details claimed that they “may have downloaded a virus on one or more of your devices” (phishing emails adopt a similar approach).
The message, which was sent several times (during different times of the day) to the same customers from a seemingly official address (info@consumer.talktalkplc.com), continued: “Unfortunately, we’ve detected a potential threat on one or more of your smartphones, tablets or computers. This may have come from an unsafe attachment, a phishing website or many other places, so we recommend you protect your devices to make sure any viruses you have are removed now.”
At this point the message recommends that subscribers enable TalkTalk’s F-Secure based SuperSafe boost, which is an anti-virus software solution that is provided free with every package for use with one device (you can increase this up to 8 devices by upgrading to the Supersafe Boost but it’ll cost you +£2 extra a month). A copy of the email has been pasted below and we will continue our report beneath.
Advertisement
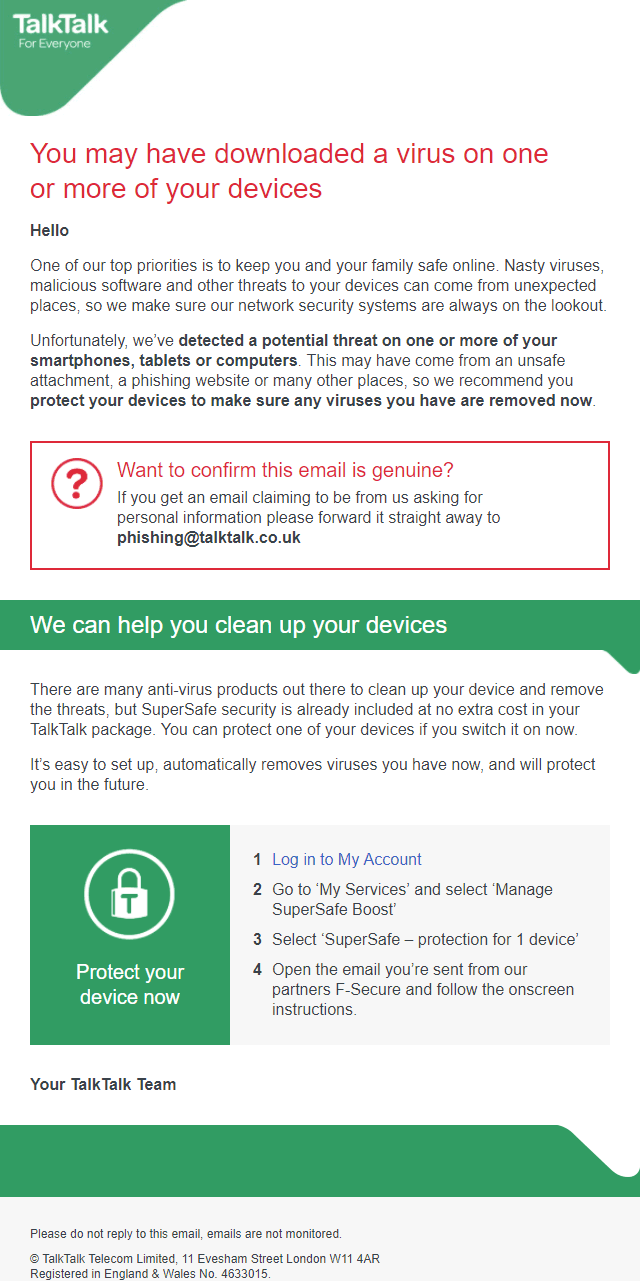
Suffice to say that the vague email resulted in a number of customers scrambling to conduct wider malware and anti-virus scans, except after several hours none of them found any such infections on their devices (note: this does not necessarily mean that a problem doesn’t exist, only that the users couldn’t find anything with their existing tools).
Related users promptly took to the ISP’s community forum (here, here and here) and began questioning whether the warnings were real or fake (phishing). Subscribers were equally curious as to how TalkTalk would even know if a virus had infected their system(s), which might raise one or two not insignificant issues about user privacy and monitoring.
TalkTalk Customer, Gondola, said:
“Well, info@consumer.talktalkplc.com is a genuine TalkTalk marketing / informational email. So based on the evidence so far it’s looking more and more like a badly conceived marketing effort that’s wasting all our time with a direct implication that a virus or malware has been downloaded.
Of course this means that the next time we receive a real warning there’s a real threat…people will ignore it. I’m not impressed TalkTalk.”
TalkTalk Customer, Marshals, said:
“The body of the email makes a specific claim that TT has detected a potential threat on one of my devices. There’s no equivocation there. So, I want to know what that potential threat is, so that I can act on it.
If this turns out to be a marketing campaign, and there never was any potential threat, TT will come out worse than when customer details were leaked. Lying to frighten your own customers does not look good.”
TalkTalk Customer, kobaltx, said:
“Today received e-mail from TT saying they had detected a virus on one of my devices and should go to my account and turn on F-Secure. This has been turned on for more than a year and account is still valid. Scanning my computer (this is the only way i contact TT) with F- Secure, Hitman Pro, Malwarebytes and MS Malware removal tool all turned up clean. I hesitate to report it as phishing as i recently renewed my contract and it may be a follow up thing.”
TalkTalk Customer, ITTroll, said:
“I received two copies of the same email today from TalkTalk … No specific details were provided and all very vague. I do not have Super Safe or Home Safe enabled. So this is either a fearmongering marketing email to upsell F-Secure, or TalkTalk have been monitoring my browsing and determined that I may have visited a potentially malicious site. Neither is particularly good.”
Initially the ISP’s community team responded to say they “can’t see anything [to say] that this came from [TalkTalk]“, although shortly after this they did confirm that it was “a genuine TalkTalk message” and after a few more hours an official statement finally dropped (below). In addition, the ISP noted that the message was only supposed to be sent once to each relevant user and that the repetition was done in error.
Official TalkTalk Statement
“One of our top priorities is keeping you and your family safe online, our Homesafe and Supersafe products helps keep you and your devices protected. Whilst we don’t monitor our customers internet traffic, our next generation DNS platform is able to identify traffic patterns from malware and potential threats on the network enabling us to notify our customers.”
We have seen other ISPs use similar detection methods before, such as when identifying whether specific subscribers are using a compromised (hacked) broadband router (these often change the DNS settings of the device and thus make a noticeable diversion in traffic flow etc.). Nevertheless in this case customers, including both those with and without HomeSafe and / or SuperSafe enabled, appeared to be receiving the same message.
Advertisement
The original message was quite specific in claiming that it had “detected a potential threat on one or more of your [devices],” although in the above statement they could just as easily be pointing the finger toward users who simply visited a bad website (even good websites can be marked bad by anti-virus firms, such as when they become briefly affected by a virus). Sadly TalkTalk failed to provide any useful detail to help users identify the true cause.
Some readers may recall that TalkTalk’s HomeSafe web filtering and monitoring system caused a bit of a privacy stir back in 2010 after customers noted that it was monitoring every URL (website address) they visited (here), even when they had chosen to disable it.
The ISP eventually responded to clarify that, “Our scanning engines receive no knowledge about which users visited what sites (e.g. telephone number, account number, IP address), nor do they store any data for us to cross-reference this back to our customers. We are not interested in who has visited which site – we are simply scanning a list of sites which our customers, as a whole internet community, have visited.”
The question now is whether or not TalkTalk have done a u-turn on the above commitment and we are still awaiting their response on that. All of this is occurring at a time when issues of internet privacy have become a hot topic in the news, not least due to the recent Facebook fiasco but also the forthcoming GDPR laws and fears of Russian hacking.
Advertisement
A TalkTalk Spokesperson told ISPreview.co.uk:
“We are continually investing in new ways to protect our customers and helping them to keep their devices free from malware is a top priority for us.
Our systems are able to identify devices that may have been infected with malware if they’ve connected to our network. These checks are done in the background and at no point do we monitor customers’ browsing history. Our recent awareness campaign was launched to inform our customers of the potential risks and provide tips on how to clean up their devices. We think it’s the right thing to do, so that our customers can keep their devices safe and running as well as they possibly can.”
Lest we forget that the government’s new Investigator Powers Act (IPA) does require larger ISPs to retain Internet Connection Records (ICR) for 12 months (assuming the code for this is ever finalised), which will include basic information about which IP addresses / servers / websites you’ve visited. All of this raises some interesting questions about the future approach by ISPs to user privacy and security, not least of which is where to draw the line.
However, if any ISPs are going to issue a message that runs the risk of scaremongering their users into thinking they have a virus on their computer, then at least give them a bit of useful detail about precisely what was detected so they know where to look (or even whether to bother looking at all). Otherwise such messages may end up looking too much like phishing or a poorly executed marketing exercise.
UPDATE 1:02pm
Added a new comment from TalkTalk above.
UPDATE 4:34pm
TalkTalk has tweaked their above statement slightly to clarify that they don’t identify the individual devices affected but do know it’s a device connected to their systems.
Mark is a professional technology writer, IT consultant and computer engineer from Dorset (England), he also founded ISPreview in 1999 and enjoys analysing the latest telecoms and broadband developments. Find me on X (Twitter), Mastodon, Facebook, BlueSky, Threads.net and Linkedin.
« UK and EU Mobile Broadband Speeds Fall While Roaming Q1 2018

















































Comments are closed