Big UK Broadband ISPs Have Big Concerns About DNS over HTTPS
A significant change is on the way that could improve the security of the internet’s Domain Name System (DNS) by adopting DNS over HTTPS (DoH), although this could also create lots of new problems for broadband ISPs and mobile operators (e.g. disrupting UK Government required censorship systems) that may be hard to overcome.
At present the existing Domain Name System (DNS) works to convert Internet Protocol (IP) addresses into a human readable form (e.g. 123.56.32.1 to examplefakeblah.co.uk) and back again. Most of the time your ISP runs the DNS servers, but advanced end-users can also tweak their own devices (e.g. routers) to use third-party DNS solutions like OpenDNS or Google’s Public DNS (i.e. taking some control away from your ISP but as these services are often unencrypted then your ISP can still intercept the data).
Unfortunately standard DNS systems do have plenty of vulnerabilities, such as situations where hackers can intercept your internet traffic through man-in-the-middle style attacks (e.g. eavesdropping, manipulation of DNS data or even blocking/censorship). Malicious actors target this method because end-users are often left none the wiser when it occurs (a very stealthy vulnerability to exploit).
Advertisement
In order to resolve this a new standard is being fast-tracked through the IETF called DNS over HTTPS (DoH). Anybody with some basic IT knowledge will recognise HTTPS as being the encrypted protocol that many modern websites use to help keep your connection to them secure from prying eyes (e.g. https://www.ispreview.co.uk is encrypted, while using http:// would be unencrypted).
The idea behind DoH is thus a simple one, with DNS requests being sent via HTTPS, sharing port 443 and secured via TLS as defined in IETF RFC 8484. The result is an encryption based protocol that has good privacy and security intentions, which is something that broadband ISPs do welcome as being of wider benefit to their users. This is of course assuming you trust the third-party DoH providers (see below).
Sounds good, so what’s the problem with DoH?
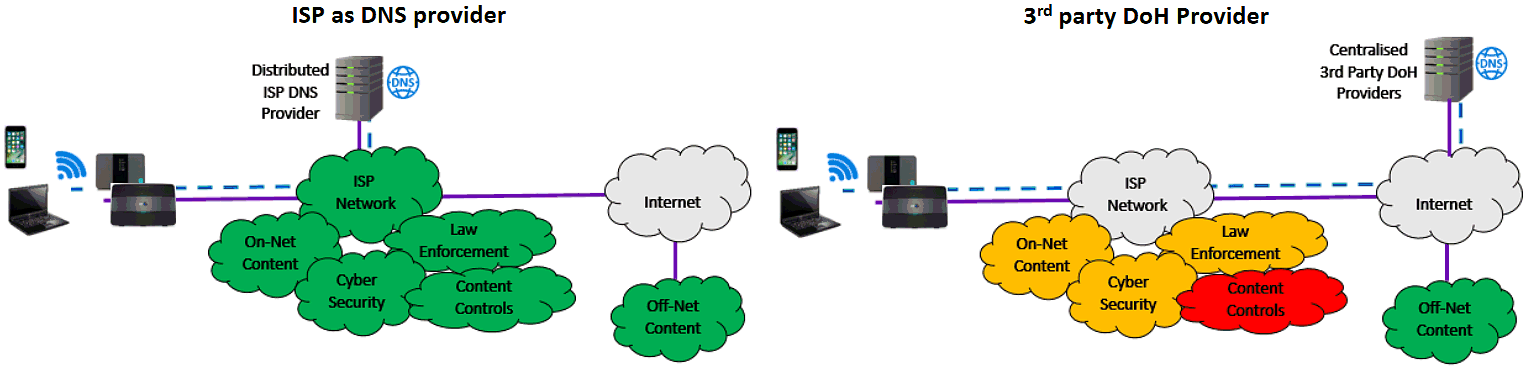
In order to work its magic DoH needs to function a bit differently from the normal DNS system and early adoption of this is also likely to be driven through centralised 3rd party DoH providers (e.g. Google, Cloudflare and Mozilla), effectively bypassing wider ISP capabilities that are dependent upon the existing DNS setup.
For example, Mozilla’s Firefox browser (since v62) has implemented DoH to automatically handle your DNS requests, although at present it’s not enabled by default (you have to activate it manually), but in the future that will change (developments around the DoH standard are still somewhat of a work-in-progress but we’d expect many more companies to follow).
Advertisement
In this setup the end-user (that’s you, dear reader) no longer has to worry about manually configuring their DNS settings to use a third-party provider. Instead the system is both encrypted and handled automatically by your web browser or other system. Essentially a significant security and privacy improvement, albeit without you having to do anything to benefit!
Firefox Statement
For more than 30 years, DNS has served as a key mechanism for accessing sites and services on the web. Browsers (including Firefox) use DNS to access a distributed database that turns URLs into TCP/IP addressing information. Firefox cannot do much without the service. DNS hails from the days of a kinder, more gentle Internet where it was normal to make this kind of query using unencrypted protocols and send them to any nearby server who claimed to be able to answer it.
This approach is no longer a fit for the modern Internet. Because there is no encryption, other devices along the way might collect (or even block or change) this data too. DNS lookups are sent to servers that can spy on your website browsing history without either informing you or publishing a policy about what they do with that information.
The downside of this approach to DoH (if you can call it a downside, as for others it’s more of an upside), at least from an ISP’s perspective, is that your DNS queries won’t hit the broadband provider’s own nameservers anymore and the provider itself would also struggle to separate out DoH from regular HTTPS traffic.
On top of that each application (e.g. Firefox) would now be able to select their own DoH provider, as opposed to a single ISP / DNS setting being used by the majority of users for every application and device. The DoH approach can thus create a number of problems with network management and control, particularly for the largest ISPs like BT, Sky Broadband, TalkTalk and Virgin Media.
Now it gets complicated
The ability to see browsing / application requests at a household level means that many ISPs can make some use of standard DNS for performing tasks like internet filtering (i.e. blocking / censoring websites – such as due to parental controls and anti-malware features or legal requirements) and identifying bad (malware) traffic. But it goes much further than that.
Advertisement
Mark is a professional technology writer, IT consultant and computer engineer from Dorset (England), he also founded ISPreview in 1999 and enjoys analysing the latest telecoms and broadband developments. Find me on X (Twitter), Mastodon, Facebook, BlueSky, Threads.net and Linkedin.
« Full Fibre Broadband ISP Hyperoptic Hail 99% Day One Success Rate
















































Comments are closed