Cross-Party Inquiry Finds UK Unprepared for Attacks on Subsea Fibre Cables

The Joint Committee on the National Security Strategy (JCNSS) has today published the results of their cross-party inquiry into the growing threats facing the country’s undersea fibre optic data cables. The report finds that the UK has “plenty of cable routes and good repair processes” for routine breakages, but the UK can’t protect all of it from adversaries and must improve.
Damage to submarine cables is, sadly, not uncommon. According to the United Nations ICPC (here), an average of 150 to 200 faults occur globally each year and require about three cable repairs per week. In addition, it usually takes a few weeks to fix a break, but this depends upon the type of break, its depth, weather conditions and various other factors.
Most of the cable breaks occur due to accidents by deep sea fishing trawlers, as well as ships accidentally dragging their anchor over them. Not to mention abrasion, equipment failure or marine life deciding to take a nibble (the latter is only really an issue for smaller / older cables that haven’t been buried). But over the past year, the act of deliberate sabotage has also become a much more real concern (example).
Advertisement
Meanwhile, the existing Submarine Telegraph Act 1885 can only impose a £1,000 fine, which is hardly much of a deterrent against costly cable damage accidents related to negligence or even sabotage, particularly those that occur in the gray zone of conflict (e.g. deliberately using civilian vessels to cause damage). Not to mention the problem of extending any law beyond the UK’s territorial waters.
Findings of the inquiry
The new inquiry found some things to commend. The UK has “plenty of cable routes and good repair processes for business-as-usual breakages“. Ministers and officials are also said to be working with industry on mitigating risks; schemes to monitor cables are gathering pace and plans to test resilience are maturing. But security vulnerabilities remain a significant problem.
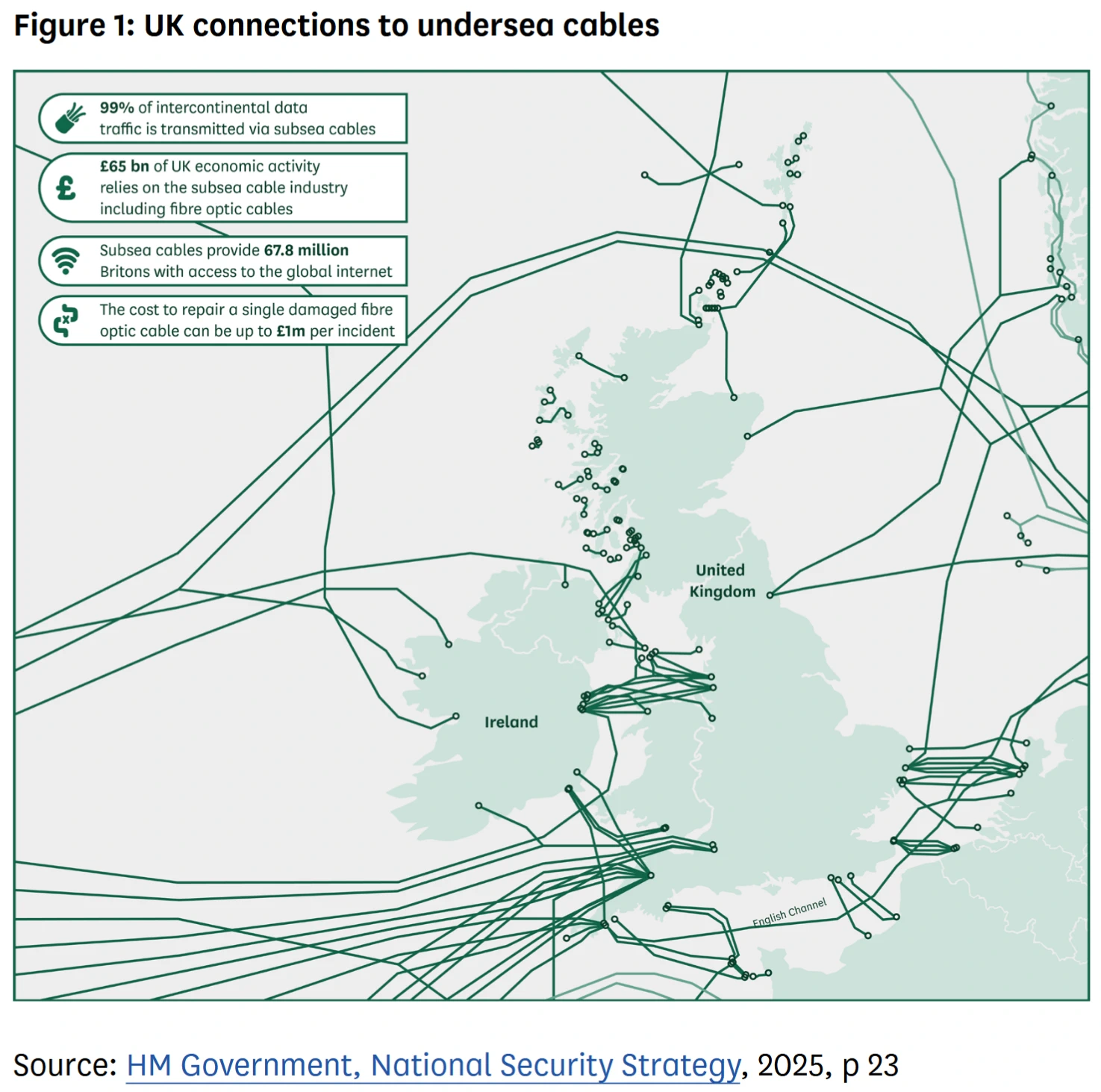
In particular, the inquiry noted how “there is a limit to how much cables can be protected from adversaries using civilian vessels to ‘accidentally’ drag anchors over the seabed“. It also noted how there are particular vulnerabilities around the UK’s outlying islands, military cables and the financial sector. The trend towards critical amounts of data – supplying home and business broadband users – being concentrated in new high-capacity cables is also expected to create a small set of “high-value targets“.
Advertisement
Onshore infrastructure is a further concern. Cables come ashore via landing stations, which remain “vulnerable to unsophisticated sabotage“. Many onward terrestrial links converge towards data centres, creating “worrying levels of concentration … This all presents risks for low-level deniable attacks which – while not causing national disruption – would be costly, provocative and hard to prevent,” said the report.
Extract from the Summary
We were disturbed about the level of scepticism we encountered in some parts of industry and government about the value of preparing for more extensive co-ordinated attacks. Some suggested we should focus on fishing accidents or low-level hybrid sabotage. We are not persuaded that this is a good basis for mitigating catastrophic risk: there needs to be a much clearer acceptance about the UK’s strategic vulnerability in the event of hostilities.
We agree that severe disruption risks are low, and hype is unhelpful. Extensive damage is not likely outside a period of heightened tension. But given the deteriorating security environment and the UK’s growing military role in Europe, we can no longer rule out the possibility of UK infrastructure being targeted in a crisis. We are also not confident that the UK could prevent such attacks or recover within an acceptable time period.
We accept that individual industry operators have few incentives to advocate costly resilience measures for a crisis that may never come. The Government, by contrast, has a duty to prepare competently for low-likelihood high-impact events. We caution strongly against the Department for Science, Innovation and Technology favouring a ‘business as usual’ industry view of aggregate national security risk.
We also believe the Government’s resilience concept focuses too much on having ‘lots of cables’ and pays insufficient attention to the system’s actual ability to absorb unexpected shocks. We found general uncertainty about how much damage the system can sustain before data stops rerouting properly. We estimate the impacts of data rerouting failures would vary across sectors, ranging from moderate to catastrophic.
The reality today is that cutting lots of transatlantic fibre optic cables within the same short period of time, while a risk, is something that would be both extremely difficult to completely prevent and to actually carry out. On the other hand, the more such attacks take place, the greater the strain on limited resources for repairs, which could result in a build-up of cumulative delays and thus connectivity problems.
The same sort of attacks and strategies could then of course be used against an aggressor. The fact that so much international trade is carried over the internet also means that other countries are likely to be harmed by such an activity, which in a conflict may end up including the attacking state or its allies to some extent (i.e. directly or indirectly).
Nevertheless, the report is right to push for improvements, and it includes a useful list of recommendations, which we’ve summarised below. The government are will probably take this onboard as they draft new laws to better address the growing risk of deliberate sabotage against our vital subsea fibre optic cables.
Advertisement
Report Recommendations
➤ The Government should update its public and private risk scenarios to cover extensive co-ordinated sabotage to subsea and terrestrial internet infrastructure, including onward connections to Europe.
➤ The National Protective Security Authority (NPSA) and National Cyber Security Centre should require all UK landing stations to be target-hardened to sufficient levels to deter state-backed sabotage. They should require landing station operators to develop within 12 months an emergency ‘good enough’ repair plan to recover from co-ordinated attacks. The NPSA should also conduct a similar exercise with European counterparts for relevant landing stations on the continent.
➤ To help mitigate risks around the clustering of high value targets, the Government should encourage subsea cable providers to connect to landing stations, terrestrial routes and data centres outside high-concentration points.
➤ The Government’s resilience plans should focus in more detail on the level of immediately available capacity in the cable system during a security crisis. The Department for Science, Innovation and Technology should request operators to provide regular updates on the scale and type of data each cable carries, short notice rerouting capacity and their ability to prioritise critical services. It should further develop detailed contingency plans for rerouting data through the Channel Tunnel, including in scenarios where high-concentration terrestrial routes are temporarily disabled.
➤The Government should acquire a genuinely sovereign cable repair ship by 2030. This could be leased to industry on favourable terms during peacetime and made available for Government use in a crisis. The Government should set out a timetable for this in response to this Report.
➤ The Royal Navy should establish a cadre of reservists and serving personnel to learn cable repair skills on commercial repair vessels. These could be called on in periods of heightened tension.
➤The Department for Science, Innovation and Technology should ensure all lead departments have detailed sector-by-sector technical impact studies on areas most likely to be affected and response plans—notably finance, maritime and air traffic, communications, defence and supply chains including food and fuel. We suggest such assessments are handled securely given their value to hostile actors. We note that some cascading impacts may not be immediately obvious—it may therefore be helpful to begin with an underpinning assessment of internet failure modes and how this would affect critical systems. The Cabinet Office resilience teams could usefully help to co-ordinate and audit these assessments.
➤ Emergency services should ensure their business continuity plans highlight any areas of critical reliance on foreign internet servers, and account for temporary internet disruption in the event of a security crisis.
➤ The Government’s review of legislation must pay particular attention to strong deterrents, such as major fines and criminal liability, that can be applied to private actors suspected of working for or on behalf of foreign states.
➤ The Government should explore new options for taking a more robust approach to interdicting suspicious vessels—for example applying piracy provisions to cables that land in the UK or seeking a limited extension of domestic criminal law jurisdiction. It should commission a legal opinion on options and risks, and publish this within six months for consultation with industry and international partners. The Government should, however, remain cautious about the risks of reciprocal action from adversaries and we do not endorse any particular option at this stage.
➤ The Foreign, Commonwealth and Development Office and the Department for Business and Trade should apply diplomatic and economic pressure to press for adequate investigations from flag states and states where vessels suspected of cable damage enter port. The Government should also work with partners, particularly the International Maritime Organization, to make greater use of port state controls as a deterrent—for example by expanding mechanisms to share data on vessels’ behaviour at sea and ensuring these are then thoroughly integrated into port inspections.
➤ The Government should support the subsea cable industry in rolling out more extensive cable monitoring technology and should explore incentives to encourage such investment. This could include Government commitments to make better use of existing measures and data—for example more proactive identification and investigation of vessels switching off Automatic Identification Systems. We also encourage industry to engage closely with the Ministry of Defence to ensure underwater monitoring does not unduly compromise defence activity.
➤ The UK’s military deterrence concepts are too timid. They need to place greater emphasis on prevention and punitive consequences that go beyond private or public attribution. Otherwise, aggressors that are content with ‘implausible deniability’ can cause damage with minimal risk to themselves. The Government should work with NATO to ensure that monitoring schemes are designed to enable speedy data sharing with law enforcement authorities—which in turn should support timely investigations, and more direct physical interdiction and prosecution where needed.
➤ The Ministry of Defence should work with international partners to ensure there are viable plans to escort cable ships without degrading wider NATO taskings. This plan could usefully include heightened surveillance of suspicious vessel activity, rules of engagement enabling a low threshold for physical interdiction of civilian and autonomous vessels, and input from industry. The Royal Navy should also practice live escorting exercises with cable repair ships to build confidence about their deployment in a security crisis.
➤ The Government should seek to provide a joined-up subsea cables function providing a centralised point of contact for industry and international partners. This body should co-ordinate, not duplicate, cross-government work—bringing together departments and agencies covering subsea infrastructure operations, policy, security, resilience and contingency planning. In the first instance this could involve upgrading the Subsea Infrastructure Response Group into a formal, standing co-ordination and oversight body, reporting into an inter-ministerial group jointly led by the Department for Science, Innovation and Technology and the Ministry of Defence
➤ The Government should further explore cable protection zones for critical areas of cable concentration, policed by early warning indicators and heightened monitoring and response capabilities. This would require close co-operation with European partners, given the need to manage other maritime activities proportionately.
Mark is a professional technology writer, IT consultant and computer engineer from Dorset (England), he also founded ISPreview in 1999 and enjoys analysing the latest telecoms and broadband developments. Find me on X (Twitter), Mastodon, Facebook, BlueSky, Threads.net and Linkedin.
« Welsh Full Fibre Broadband ISP Ogi Confirms Departure of Current CEO UPDATE






















































Comments are closed