Google Public DNS Internet Traffic Hijacked and Redirected to BT Latin America

Internet users that have chosen to replace their broadband ISPs own Domain Name Servers (DNS) with Google’s free Public DNS alternative, which translates IP addresses into human readable form and vice versa, had a bit of a shock over the weekend when their traffic was redirected (hijacked) and sent to BT’s Latin America division in Venezuela and Brazil.
DNS servers are a key component of the Internet and most ISPs use them to covert IP addresses (e.g. 123.56.23.89 [IPv4 example]) into a domain name (e.g. happycatsrus.uk) and back again. But sometimes the ISPs DNS servers can be slower than ideal or may do other things that annoy you (e.g. hijack your Internet searches), in those situations Google and others (e.g. OpenDNS) offer a free alternative.
Advertisement
However Monitoring firm BGPmon, which helps people and operators to assess the routing health of their network, noted in a brief update yesterday afternoon that the Internet search giant’s Public DNS service (8.8.8.8/32) was “hijacked for [around] 22 minutes yesterday [saturday], affecting networks in Brazil & Venezuela“.
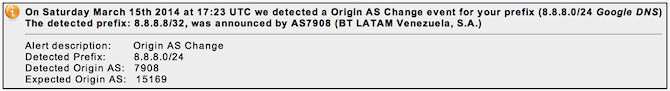
The situation looks like it might have been caused by a BGP (Border Gateway Protocol) hijack, which is regarded as a somewhat significant man-in-the-middle attack / security vulnerability in the worldwide Internet traffic-routing system.
Last May 2013 it was revealed that someone had been using a similar method to stealthily hijack Internet traffic bound for the USA / other countries and redirecting it through servers in Belarus and Iceland, before sending the traffic back on its way to the original destination.
The phenomenon appears to have become increasingly common and the latest redirect didn’t seem to have any problem with getting around Google’s DNSsec security policies. But this alone might not be adequate protection against hijacks, unless Google are also using the latest Resource Certification (aka – Resource Public Key Infrastructure) and other measures to prevent untrusted sources from making such a big change.
Advertisement
At this stage it’s unclear why Google’s Public DNS traffic, which handles around 150 billion queries a day from close to 100 million unique IP addresses, was incorrectly redirected / hijacked and sent off towards BT’s Latin America division. We have shot off a message to Google’s PR division in the hope of finding an answer.
It should be noted that BGP hijacks are now an almost daily occurrence, although most of these don’t hurt traffic on a global level. Similarly it should be noted that Google’s Public DNS service has been hijacked a few times before, such as in 2010 when their traffic was redirected to Romania and Austria.
Mark is a professional technology writer, IT consultant and computer engineer from Dorset (England), he also founded ISPreview in 1999 and enjoys analysing the latest telecoms and broadband developments. Find me on X (Twitter), Mastodon, Facebook, BlueSky, Threads.net and Linkedin.
« Hampshire UK Reveal Spring 2014 BDUK and BT FTTC Broadband Rollout




















































Comments are closed