UPD Hackers Hijack 300K Home and Office Broadband Routers from Big Brands

Researchers working for Team Cymru’s Threat Intelligence Group have discovered that over 300,000 consumer-grade small office / home (SOHO) broadband routers, including those from brands like ZyXEL, D-Link, Micronet, Tenda, TP-Link and others, have been hijacked as part of a man-in-the-middle style attack.
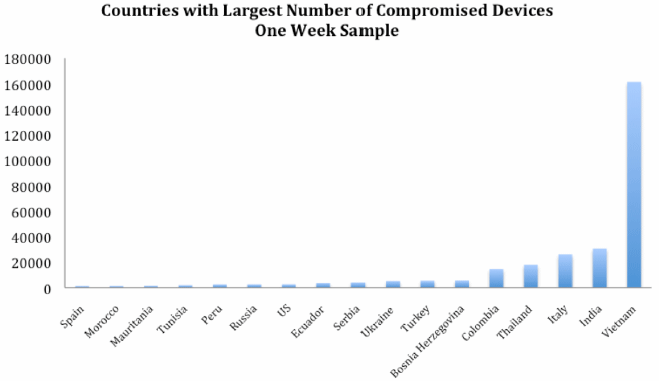
The affected devices, which have been spotted all over the world (mostly Vietnam), were found to be vulnerable to multiple exploit techniques, including a recently disclosed authentication bypass vulnerability in ZyXEL’s ZynOS firmware and Cross-Site Request Forgery (CSRF) techniques similar to those reported in late 2013.
Advertisement
Apparently the attackers exploit these known flaws to access the devices and alter their Domain Name System (DNS) configurations in order to redirect the victims DNS requests (e.g. a DNS request is made when you want to visit a website) and subsequently replace the intended answers with IP addresses and domains controlled by the attackers (a Man-in-the-Middle attack).
Hacker’s DNS Settings
Primary IP: 5.45.75.11
Secondary IP: 5.45.75.36
Once compromised the hacker can effectively snoop on all of your primary online activity, such as by recording your key presses as you login to your online bank account. On top of this the DNS servers appear to be controlled by a London-registered hosting firm (3NT Solutions), although the actual servers appear to be based in the Netherlands and not the United Kingdom.
The good news is that the UK itself doesn’t really crop up much in the count of infected devices, with victims being spread globally and most likely distributed based on the proportion of vulnerable devices supplied by local ISPs.
The easiest way to tell if you’ve been compromised is to login to your router via a web browser and check what, if any, IP addresses have been assigned for your Internet connections DNS servers. This is often set to automatic and controlled by your ISP, although others may be legitimate DNS settings for OpenDNS (208.67.222.222 and 208.67.220.220) or Google Public DNS (8.8.8.8 and 8.8.4.4) etc.
Advertisement
But if any of these IPs happen to match the hacker addresses listed above then swap them for something more legitimate and make sure your router has the latest firmware installed (note: ISP supplied kit usually gets updated automatically). Details of the hack can be found in the teams report.
UPDATE 6th March 2014
A status update from AAISP (here) reveals that the broadband provider has received a “small number of reports from customers who have had the DNS settings on their routers altered. The IPs we are seeing set are 199.223.215.157 and 199.223.212.99 (there may be others)“. This is a related DNS exploit that was also mentioned in the above report.
The ISP spotted the activity by logging when customers tried to access the related IP addresses and contacting them accordingly. We only wish other ISPs would confirm if they were also being this pro-active.
Advertisement
Mark is a professional technology writer, IT consultant and computer engineer from Dorset (England), he also founded ISPreview in 1999 and enjoys analysing the latest telecoms and broadband developments. Find me on X (Twitter), Mastodon, Facebook, BlueSky, Threads.net and Linkedin.
« ISP Gigaclear Win Contract to Deploy FTTP in Northmoor with RCBF Money





















































Comments are closed