24 Million Home Routers and ISPs Open to DNS DDoS Amplification Attacks

A new report from Nominum, which provides ISPs with DNS based analytics and monetization solutions, has claimed that 24 million home broadband routers, including many in the UK, could be exposing ISPs and their users to becoming unwitting participants in massive Internet DNS-based Distributed Denial of Service (DDoS) attacks.
Most DDoS attacks work by overloading a target server (e.g. a website or other online service) with masses of data requests from multiple internet connected computers; usually Trojan/Virus infected computers that then become part of a botnet. But recently the new target has become home broadband routers, especially older models that are no longer updated or which lack good security.
Advertisement
A hacker doesn’t want to use their own system to attack others and risk discovery, thus they launch DDoS attacks from remote systems on which they’ve gained unauthorized administrative control. But in this instance the attacker seeks to manipulate Domain Name System (DNS) traffic, which translates IP addresses into human readable form (e.g. ‘123.45.67.32’ > ‘mywebsite.com’), and they might not even need to hack your router in order to do it.
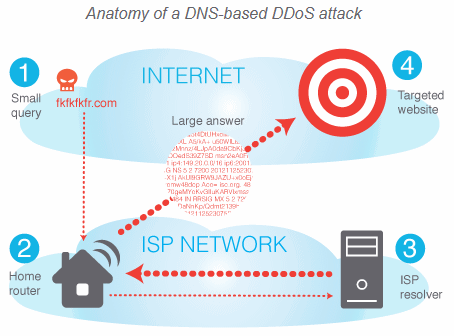
In short, the attacker will spoof (pretend to be from) their targets IP address and then send a very small request (ICMP) to a vulnerable home router / network (i.e. one that allows open DNS proxies / resolvers). Being a nice chap the server will respond but it does so by sending a larger packet of data back to the real IP address.
It’s a simple method and one that can be multiplied across thousands or even millions of connections, potentially giving somebody with a single 1Mbps line Gigabits of data to use when overwhelming the target server.
Sanjay Kapoor, Nominum’s CMO and SVP of Strategy, said:
“Existing in-place DDoS defenses do not work against today’s amplification attacks, which can be launched by any criminal who wants to achieve maximum damage with minimum effort. Even if ISPs employ best practices to protect their networks, they can still become victims, thanks to the inherent vulnerability in open DNS proxies.
ISPs today need more effective protections built-in to DNS servers. Modern DNS servers can precisely target attack traffic without impacting any legitimate DNS traffic. ThreatAvert combined with ‘best in class’ GIX portfolio overcomes gaps in DDoS defenses, enabling ISPs to constantly adapt as attackers change their exploits, and precision policies surgically remove malicious traffic.”
A related report on The Guardian today suggests that 800,000 home routers belonging to customers of ISPs in the United Kingdom, such as Virgin Media and BT, could allegedly be vulnerable to this type of exploit, turning their customers into pawns for a wide-scale attack.
Advertisement
Nominum’s report notes that an attack in January 2014 showed how more than 70% of total DNS traffic on a provider’s network was associated with DNS amplification. A second attack in February found that more than 5.3 million routers were used to generate attack traffic.
The solution is to ensure that a DNS resolver only responds to queries from authorized clients and more information on how to do that can be found here. Ultimately this is an issue for the ISPs to take the lead in addressing but a good router / firewall can also provide a front-line level of defence.
Separately it’s also become increasingly common for hackers to infiltrate a router and then add custom DNS settings to the device, which is precisely what happened last month when 300,000 routers were hijacked; including some being used by customers of PlusNet and AAISP in the UK (here). But that’s less about conducting DDoS attacks and more about stealing your personal data.
Mark is a professional technology writer, IT consultant and computer engineer from Dorset (England), he also founded ISPreview in 1999 and enjoys analysing the latest telecoms and broadband developments. Find me on X (Twitter), Mastodon, Facebook, BlueSky, Threads.net and Linkedin.
« UK ISP TalkTalk Slows Access to Imgur.com Website After IWF Block





















































Comments are closed