Cloudflare Ignite Consumer ISP Confusion with BGP Safety Test
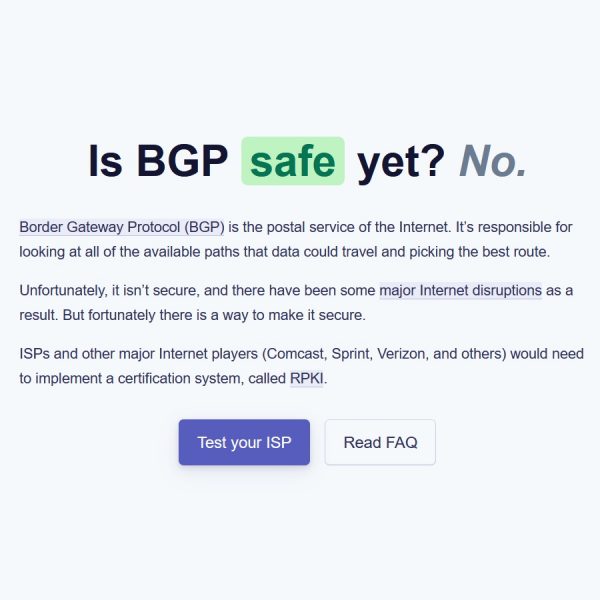
Over the past few days we’ve had a small but growing stream of Tweets and Emails from people who have run Cloudflare’s new ‘Is BGP Safe Yet‘ tool and are worried that their UK broadband ISP is “unsafe” because it uses the Border Gateway Protocol (BGP) and not RPKI. Aside from poor timing with COVID-19, the result can be misleading.
The Border Gateway Protocol (BGP) system is a protocol that helps to link the internet together by exchanging routing information with Autonomous Systems (AS), such as those run by your ISP (each provider will have many peers and routes to send data). Networks around the world need to talk to each other in order to do peering and determine which routes are the best ones for them to send their data, which is what BGP facilitates.
BGP is normally one of those things that works seamlessly in the background and there are a lot of very technical aspects to it, which is just one of many reasons why launching an oversimplified checking tool – seemingly aimed at ordinary non-tech savvy consumers – could be counter-productive. Likewise doing this during a global pandemic, when network operators have much bigger problems to focus on, doesn’t seem terribly helpful.
Advertisement
The risk is that some people may assume that what the website is telling them is the only truth and become concerned for their online security (a fact born out by the messages we’ve recieved). Indeed at present most ISPs will probably return results like the ones below from UK providers, which Cloudflare then asks you to spam spread via social media as part of their marketing campaign.
FAILURE
Your ISP (Sky Broadband, AS5607) does not implement BGP safely. It should be using RPKI to protect the Internet from BGP hijacks.
FAILURE
Your ISP (THREE UK, AS206067, AS206067) does not implement BGP safely. It should be using RPKI to protect the Internet from BGP hijacks.
FAILURE
Your ISP (Virgin Media Business, AS5089) does not implement BGP safely. It should be using RPKI to protect the Internet from BGP hijacks.
Sadly it is indeed true to say that BGP does have its problems, not least because it relies upon a degree of trust between networks. Sometimes network operators can make mistakes (e.g. human error), which may result in them announcing incorrect routes and that can send a lot of traffic off in the wrong direction, causing all sorts of problems. Similarly other networks may abuse this trust to hijack traffic for malicious purposes.
Over the years various changes and attempts have been made in order to tackle such challenges. One of the most recent is Resource Public Key Infrastructure (RPKI), which as Cloudflare says is a “security framework method that associates a route with an autonomous system. It uses cryptography in order to validate the information before being passed onto the routers.”
Louis Poinsignon, Cloudfare, said:
“BGP leaks and hijacks have been accepted as an unavoidable part of the Internet for far too long. We relied on protection at the upper layers like TLS and DNSSEC to ensure an untampered delivery of packets, but a hijacked route often results in an unreachable IP address. Which results in an Internet outage.
The Internet is too vital to allow this known problem to continue any longer. It’s time networks prevented leaks and hijacks from having any impact. It’s time to make BGP safe. No more excuses.
Border Gateway Protocol (BGP), a protocol to exchange routes has existed and evolved since the 1980s. Over the years it has had security features. The most notable security addition is Resource Public Key Infrastructure (RPKI), a security framework for routing. It has been the subject of a few blog posts following our deployment in mid-2018.
Today, the industry considers RPKI mature enough for widespread use, with a sufficient ecosystem of software and tools, including tools we’ve written and open sourced. We have fully deployed Origin Validation on all our BGP sessions with our peers and signed our prefixes.
However, the Internet can only be safe if the major network operators deploy RPKI. Those networks have the ability to spread a leak or hijack far and wide and it’s vital that they take a part in stamping out the scourge of BGP problems whether inadvertent or deliberate.”
The intention of Cloudflare’s tool, which is to make BGP more secure by encouraging adoption of RPKI, is a noble one but it does seem to be causing some unnecessary panic. Firstly, just to clear up one confusion that has surfaced as a result of this tool, RPKI is a complement to BGP and NOT a replacement (RPKI is effectively a cryptographic wrapper for BGP). BGPv4 remains the primary routing protocol, which even Cloudflare uses.
Advertisement
The next issue is that implementing RPKI is a very complicated task and not the sort of thing a network operator would take on during the COVID-19 pandemic, when the risk of mistakes causing wider problems is one best avoided. A risk assessment and a lot of planning would be needed first because if you haven’t got all your ducks in a row (including peers downstream from you) then blackholing internet traffic becomes a real possibility.
In the meantime it’s probably the wrong time to loudly proclaim that most ISPs are “not secure” simply because they haven’t adopted RPKI yet. Good networks will already filter BGP announcements to ensure that the information they share is correct, although sadly some parts of the world and networks don’t do this, hence how hijacks can become a problem (these are usually rectified quite quickly).
Nevertheless for the most part BGP does its job and major problems are uncommon, if not as rare as we’d all like. As things stand the list of providers who do not yet fully implement RPKI, as shown on Cloudflare’s site, is still far larger than the list of those who do. Major players like Google, Zayo, Level3 (CenturyLink), Vodafone and Comcast have yet to do so.
Otherwise, please don’t panic if your ISP, like most providers, doesn’t yet support RPKI. We suspect that they’ll almost all get around to adopting it eventually but changing such core pieces of a network can take time and a huge amount of care. Right now, when it comes to internet security, the vanilla malware stuff like viruses, phishing, DNS hijacks and SPAM are still a much bigger threat to individual internet users.
Advertisement
The MD of UK ISP Andrews and Arnold (AAISP), Andrian Kennard, has a good blog up on all this (here). “If the major transit providers start filtering routes checking RPKI then that alone will solve the problem of rouge routes – but if they all filter what they receive anyway from customers, that would avoid the issue without RPKI,” said Adrian.
UPDATE 22nd April 2020
We note that Hyperoptic is one of several UK ISPs to have issued brief statements on this after receiving some of the same messages of concern from customers, usually following use of the tool.
HO’s Statement
“We would like to thank everyone for bringing this website to our attention. We understand your concern, but firstly, let us reassure you it is safe to use our network.
Your online security is of the utmost importance to us and we employ industry best practices to ensure BGP security is enforced.
BGP hijacking is a relatively rare security risk which has recently been publicised by companies selling solutions for it, in order to promote their own technologies (in this case RPKI).
RPKI has, as far as we know, not yet been implemented by any ISP in the UK, and by only a handful of ISPs globally. It is currently only supported by a couple of hardware vendors for network routers, and not by the majority.
In line with other ISPs, we are closely following industry developments to ensure BGP security in the future, and we will continue to use best practices.
So please rest assured that you can continue to use your Hyperoptic service as normal.”
Mark is a professional technology writer, IT consultant and computer engineer from Dorset (England), he also founded ISPreview in 1999 and enjoys analysing the latest telecoms and broadband developments. Find me on X (Twitter), Mastodon, Facebook, BlueSky, Threads.net and Linkedin.
« Cityfibre’s 1Gbps FTTH Broadband Goes Live in Northampton UK



















































Your ISP (Hutchison 3G UK, AS60339) does not implement BGP safely. It should be using RPKI to protect the Internet from BGP hijacks.
If a hijacked route often results in an unreachable IP address, could this be the reason Three’s customers are complaining in the forums about the high number of webpages not loading??
You’d probably hear about it in the news if a BGP hijack were to blame. Such issues are far more commonly caused by more specific problems with DNS, bad network configuration or other peering/routing problems.
No.
Here’s BT’s BGP Result
Your ISP (BTnet (BT’s UK IP Network – AS2856), AS2856) does not implement BGP safely. It should be using RPKI to protect the Internet from BGP hijacks.
Plusnet:
Your ISP (Plusnet plc, AS6871) does not implement BGP safely. It should be using RPKI to protect the Internet from BGP hijacks
As expected A&A pass,
Your ISP (Andrews & Arnold Ltd, AS20712) implements BGP safely. It correctly drops invalid prefixes.
A&A pass because. “In the mean time, having been made aware of an invalid route deliberately announced by Cloudflare, we have blocked that route manually.”
The other ISP’s should do the same.
Yeah, AAISP have hacked the Cloudflare test by manually dropping the invalid prefix Cloudflare announce on their routers.
AAISP’s MD has stated on Twitter that they are looking to develop in RPKI in their core routers, but as yet, they don’t support this.
It’s all an interesting debate!
However, until such time that the entire world – both ISPs on on-side, and the content providers on the other all support RPKI, set ROAs/route objects in a RIR, then there will still be glaring gaps in RPKI being effective at stopping prefix hijacking, (and until the next weakness is found)!
As the article points out, any ISP worth their salt filters routes by verifying it against public records that prove ownership or the right to announce and manage the prefixes in question.
Customers tend to get a bit annoyed when they wonder why we won’t accept their prefixes but other providers will. At least until they have it pointed out that it’s for everyone’s protection.
Now if every ISP was competent enough to stop route hijacking it would be much less of a problem to begin with.
Indeed. Yes, there are tier 1 transit providers that advertise basically the entire Internet, however as long as they are doing their job and properly filtering the prefixes coming from their customers all is well.
Random Russian ASN has no business advertising a /24 from Google’s ASN. If Google’s ASN doesn’t feature in the path it shouldn’t be there.
RPKI removes the need to trust that peers higher up the chain than yourselves are doing their job, too.
Seems a while ago that people used to love when someone at a public peering exchange messed up their advertisements and advertised a supernet or even a default route. It used to be considered free transit!
Don’t forget ISPs that don’t properly limit the number of prefixes either, so that if someone else does something stupid upstream and accidentally leaks a bunch of routes then that will be caught.
The problem with RPKI is that it’s got a few issues (especially in certain parts of the world), here’s some explanation from an African operator
https://www.linkedin.com/pulse/rpki-things-being-considered-andrew-alston/
I am not entirely clear why Cloudflare are going out of their way to annoy so many.
Naming, shaming and providing people who haven’t a clue what they are reading an automated way to harass their ISPs isn’t great.
ISPs have enough to do with capacity upgrades and ensuring stability right now. The engineering and, indeed, onsite resources to carry out such a program aren’t really there right now.
Don’t blame covid for everything how long ago was bgp rpki introduce 2012 or so? At least 10 incidents of bgp hijacking have happened since. How ever complicated something is not implementating security improvements are unacceptable. The June 2019 indicated for example is very disturbing to me.
Interest Virgin Media home is ok but Virgin Media Business is not:
Your ISP (Virgin Media, AS5089) implements BGP safely. It correctly drops invalid prefixes.
I think they did same as AAISP and started to cheat. https://www.ispreview.co.uk/index.php/2020/04/cloudflare-ignite-consumer-isp-confusion-with-bgp-safety-test.html#comment-221141
Virgin Media home AS5089 still accepts the Cloudflare announcement, I don’t use Virgin’s DNS though so maybe they blocked the domain on their DNS:
“Your ISP (Virgin Media, AS5089) does not implement BGP safely. It should be using RPKI to protect the Internet from BGP hijacks.”
Sorry – by bad – I use Pi-hole here and own DNS root hints and not Virgin Media’s
virgin media will get to it at the same time as IPv6.
nextyeardecade
Is this the same Cloudfare that when I had a flaky FTTC could not distinguish between errors caused by pocket loss and unsafe connections?
https://iscloudflaresafeyet.com/
https://bit.ly/2Y7tkua
Worth reading