New SSID Confusion Attack Exploits General WiFi Vulnerability

Network security researchers have published details of a new vulnerability that arises from a “design flaw” in the IEEE 802.11 WiFi standard (CVE-2023-52424), which is said to impact “all operating systems and WiFi clients” and allows an attacker to trick Wi-Fi clients into connecting to an untrusted network.
According to TOP10VPN, which teamed up with security researcher Mathy Vanhoef to share this WiFi exploit – ahead of its presentation at the WiSec ’24 conference in Seoul – the root cause of this vulnerability stems from the fact that the IEEE 802.11 standard underpinning how WiFi works does not require the network name (SSID) to always be authenticated.
In short, the attack tricks a victim into connecting to a different WiFi network than the one they intended by exploiting the lack of SSID authentication. As if to make matters worse, routers that support the latest WPA3 encryption standard may be more vulnerable than those using WPA1 or WPA2. This is because WPA3 has an optional mode where the SSID is not used to derive the Pairwise Master Key (PMK) in the SAE (Simultaneous Authentication of Equals) handshake.
Advertisement
Unfortunately, while avoiding the use of the SSID is what makes this mode highly robust against a variety of cyberattacks, it is also what makes it vulnerable to the new attack outlined in the new report. But when WPA3 incorporates the network’s SSID, the new attack will fail. Mesh WiFi networks typically also use SAE rather than 802.11X to avoid introducing a single point of failure, which means they may also be vulnerable.
How Does the Attack Work?
For the SSID Confusion attack to succeed, the following must be true:
➤ The victim wants to connect to a trusted network.
➤ There is a second network available with the same authentication credentials as the first.
➤ The attacker is within range to perform a man-in-the-middle (MitM) attack between the victim and the trusted network.
Note that the victim doesn’t need to have ever connected to the untrusted network. Nor does the attacker need to know the victim’s credentials.
Once the target (victim) has connected to a different WiFi network from the one they intended, the attacker – who controls the bad network – can then do all sorts of nasty things, such as installing malware on the client’s device or snooping on their internet traffic. Full details can be found in this report (PDF).
A successful SSID Confusion attack also causes any VPN with the functionality to auto-disable on trusted networks to turn itself off, leaving the victim’s traffic even more exposed.
Report Conclusion
We showed that users, or their apps, make security-sensitive decisions based on the network they are connected to. For instance, some VPNs can disable themselves when connected to a trusted Wi-Fi network. However, we demonstrated that a client can be tricked into unknowingly connecting to a different network, even when enterprise or home WPA3 protection is used. This is caused by a design flaw in several authentication methods defined in the 802.11 standard. This vulnerability was assigned CVE-2023-52424.
A backwards-compatible defence is to use beacon protection and to verify the authenticity of a beacon, and the network name contained in it, before exchanging data frames. Alternatively, the 802.11 standard can be updated to always authenticate the network name when connecting to a network.
The big problem here is that, in order to properly resolve this, the existing WiFi standard(s) might need some updates, which is something that may only occur for kit that is still supported by the manufacturer.
Advertisement
In the meantime, existing networks can mitigate the attack by avoiding credential reuse across SSIDs, while enterprise networks should use distinct RADIUS server CommonNames and home networks should use a unique password per SSID (i.e. not one password shared across all the SSIDs put out by your router, which is fairly common).
Mark is a professional technology writer, IT consultant and computer engineer from Dorset (England), he also founded ISPreview in 1999 and enjoys analysing the latest telecoms and broadband developments. Find me on X (Twitter), Mastodon, Facebook, BlueSky, Threads.net and Linkedin.
Gov Expanding Gigabit Broadband Vouchers to UK Urban Areas »





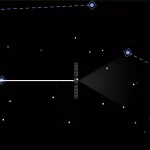














































“Once the target (victim) has connected to a different WiFi network from the one they intended, the attacker – who controls the bad network – can then do all sorts of nasty things, such as installing malware on the client’s device or snooping on their internet traffic”
Is this not mitigated to a large extent by the use of HTTPS and authentication. IMHO you shouldn’t be having devices which can be compromised via network access alone connected to any network. With Windows Linux and Android for the most part you’d need a username and password in addition, and these wouldn’t be sent in the clear
First of all this top10vpn website is throwing tls cert error, secondly:
“Once the target (victim) has connected to a different WiFi network from the one they intended, the attacker – who controls the bad network – can then do all sorts of nasty things, such as installing malware on the client’s device or snooping on their internet traffic.”
does this open an extra RCE or this is classic babble to scare non-technical people? If latter then this applies to any public WiFi network.
Kind of a non-issue to me.
For this attack to work, you need to have two SSIDs sharing the same passphrase. Let’s say a network has two SSIDs, one for internal trusted devices and one for guests, and they share the same passphrase. An attacker can rewrite beacon frames so that devices think they are connected to the internal network but are actually connected to the guest network.
The attacker doesn’t have control of the guest network since it is not an impersonation attack. The main issue is that by connecting to a network other than the expected one, it invalidates all the security assumptions a user may have.
This presumes the adversary launching the attack knows the authentication credential (e.g. SAE password) used on the target network. If that’s the case, then he can just impersonate a valid AP and attract clients, there’s no need to launch a complicated man-in-the-middle attack.
This is bogus.
There is no update to the 802.11 standard needed. As noted, just use beacon protection if you’re at all concerned about this.
WPA3 is useless to most people as the majority of devices don’t support it, certainly a lot of the smart home devices.
If I used it on my router, I would lose connection to 99% if not more of my Wi-Fi devices.
I only have one SSID anyway
yes, the point of new standards is that it takes time to percolate through. It’s considerably more secure than WPA2 and worthwhile to upgrade to eventually.
Several ISP routers support it now (either by default or can be enabled optionally) and a lot of phones/laptops will support it too, including anything that supports wifi6. You wouldn’t lose connection on 99% of devices if you enabled the transition mode that allows WPA3 and WPA2 to co-exist.
“IoT” dreck might not support WPA3, but then those devices have a host of issues anyway
The only device I have at home not supporting WPA3 is printer. WPA2 and WPA3 can work together.
If you can stick older devices that need internet access only and not other devices on network then isolate on a WPA2 SSID with device isolation.
Stick newer devices that support WPA3 on another (maybe that is for internet only and device isolation) and finally WPA3 for newer devices on another SSID that require “intranet” access/internal network/other devices. This is if you don’t have an advanced firewall that allows device specific rules and VLANS. WPA3 has enforced Protected Frames as part of its standard.
WPA2/WPA3 mixed on SSID is pointless as compromise of WPA2 means they are in usually. Obviosuly range of other stuff you can do to be secure, but network segmentation is one I’ve done.
@Ivor, but when WPA2 came about, there were a lot less Wi-Fi devices around and a lot less people on the net. My Mac supports it, but I don’t think my phone will, it is too old and my Tv will not I doubt. But I could be surprised.
None of the smart plugs will, or my smart thermostat.
Can devices be updated to it via an update, or is it hardware based? As i do have devices that are still updated like My echo dots, my cameras, philips hue hub and switch bot hub
As I have posted a few times, I tend to use Ethernet where possible, it is only stuff that don’t have a way to connect via Ethernet that I stick on Wi-fi.
idiot who can;t even put a proper username says about WPA2 and WPA3 working together, while when I activated WPA3 on my router, nothing would connect. There is a WPA3-Personal +WPA2-PSK[AES], but some stuff still would not connect, but it was when I first had the router, it has had a few updates since then, so maybe I will try again. Not that it really makes much difference, I doubt anyone here is going to try to hack into my Wi-fi, I don’t think anyone close to me would have a clue how to do it.
@ad that’s no different to when WPA2 was new though. Routers would be configured to support WPA2 and WPA1 and your device used what it could. Then things got to the stage where WPA1 could be disabled by default. It will be no different here.
It will be a combination of hardware and software and the appetite the manufacturer has towards adding features. For example, some Intel WiFi 5 (ac) cards support WPA3 if running windows 10 and the driver has been updated to a newer version. It doesn’t have to be a WiFi 6 device.
WPA3 transition mode works fine on my ISP supplied router. Another sad indictment of the state of third party retail hardware I guess.
@anonymous – not really. WPA3 transition mode still makes it harder to intercept/decrypt traffic (where the client can support WPA3) and it gets it out there and battle hardened before ISPs and router manufacturers disable WPA2 by default.
There is no need to faff around with multiple SSIDs and client isolation and all that guff – your average user isn’t getting that much attention from someone sat outside in a car.
@Ivor. Transition mode is working fine now for everything, so maybe it was either a problem with an earlier firmware in the router, or the wind was blowing the wrong way when I tried it :).
As i have posted before, my main devices are connected via Ethernet. I did think at one point of hiding my SSID, but that is a pain and to be honest, the chance of anyone getting onto my Wi-fi is pretty slim.