Some UK TalkTalk D-Link DSL-3680 Routers Vulnerable to DNS Hijack
Customers of TalkTalk’s home broadband service in the United Kingdom, specifically those who use one of the ISPs older D-Link DSL-3680 routers (check the model code on the back), should be aware that for some people the hardware might be vulnerable to an easily performed remote DNS hijack.
The DNS system works to convert IP addresses to a human readable form (e.g. 123.56.32.1 to examplefake.com) and back again. Most of the time your ISP runs the DNS servers, but end-users can also access their own computers and routers to use custom DNS solutions like OpenDNS or Google’s Public DNS.
But if a hacker gains access then they could replace the Primary and Secondary DNS settings with malicious servers. The result of a successful attack means that the hacker can redirect your website requests to fake phishing sites or monitor your activity to steal personal / financial information and inject more exploits into your home network in order to gain even greater control etc.
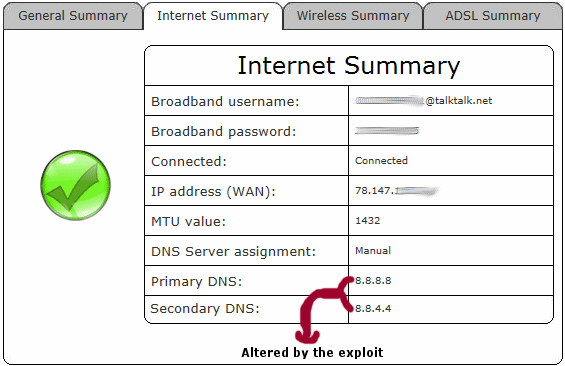
(Demo conducted by the customer – DNS was set to “auto” before the exploit attempt)
Meanwhile the problem with TalkTalk’s kit was spotted on Tuesday by a couple of customers, with one noticing that the Domain Name Server (DNS) details of their router had been changed and redirected to an unknown location without their permission (most likely a DNS server run by the attackers).
A second subscriber then tested the exploit on their DSL-3680 and found that he too was able to remotely change the DNS details of his router by merely using a special custom URL (web address) alongside the IP address of his Internet connection (no password was required). It’s a little more complicated than that, but not much.
It’s not uncommon for routers to expose their admin web-interface to the Internet, usually for purposes of remote management, although clearly it shouldn’t be this easy to crack.
John Smith, A TalkTalk Customer, told ISPreview.co.uk:
“Given that D-Link appear to have known about this for two months since the story broke, I would have imagined they would have fixed their current routers by now, including the DSL-3680.
I was shocked to see my DNS settings altered remotely by some unknown entity, as you can imagine, especially since I know I used a very strong password for remote management. But I was bothered that I could not restrict access to specific IPs [for remote management], and this issue would have been mitigated had I been able to do so.”
The exploit appears as if it could stem from a vulnerability that we first reported on in January 2015 (here), which affected a number of D-Link routers, although D-Link has been hit by similar exploits over the past few years and so that it’s hard to know which one is the actual culprit.
On top of that D-Link appears to be of the viewpoint that the 3680 is not vulnerable to such an attack, yet the code used to perform it is almost identical to the one we covered earlier this year and TalkTalk informs that they’ve asked D-Link to check again. For security reasons we have chosen not to demonstrate how this works, although it’s easily found online.
D-Link officially published a firmware update to fix the aforementioned exploit a couple of weeks ago, while the last firmware released for TalkTalk’s D-Link DSL-3680 was v1.12t on 10th November 2014 (here) and the affected customers are currently on that version. TalkTalk’s other D-Link routers include the 2680, 2640R, 2740R, 2780 and 3780.
At the time of writing TalkTalk have said that they’re still investigating the situation and we hope to have an update soon. But customers who do have the router shouldn’t worry just yet because it’s only an issue if you’ve enabled Remote Management, which is normally disabled by default. Obviously we’d recommend switching this feature off until the issue is resolved (hackers can easily scan for exposed routers, so do check).
Take note that the remote management being referenced above is not the familiar CWMP/TR-069 interface, but rather a separate feature that allows users to log into the router’s web interface over WAN (useful for remotely monitoring your network). By comparison the TR-069 feature, which is often used by ISPs to deliver firmware updates, is not vulnerable.
Mark is a professional technology writer, IT consultant and computer engineer from Dorset (England), he also founded ISPreview in 1999 and enjoys analysing the latest telecoms and broadband developments. Find me on X (Twitter), Mastodon, Facebook and Linkedin.
« BT Extends “Fibre Broadband” Rollout Contract with Emtelle to 2019
Latest UK ISP News
- FTTP (5524)
- BT (3518)
- Politics (2540)
- Openreach (2298)
- Business (2264)
- Building Digital UK (2246)
- FTTC (2044)
- Mobile Broadband (1975)
- Statistics (1788)
- 4G (1666)
- Virgin Media (1621)
- Ofcom Regulation (1463)
- Fibre Optic (1395)
- Wireless Internet (1389)
- FTTH (1381)




















































Comments are closed